SAS Government Management
Detect, prevent and more effectively manage both opportunistic and professional fraud across your organization. Precise targeting dramatically reduces false positives, ensuring that the vast majority of valid transactions continue without delay.
Detect fraud with greater precision and reduce fraud losses.
Standardize, integrate and authenticate data and consolidate program integrity activities. A robust fraud analytics engine processes all transactions (not just a sample) using multiple techniques – including automated business rules, predictive modeling, embedded AI and machine learning, text mining, search and discovery, exception reporting and network link analysis. Online, real-time scoring enables you to stop fraudulent payments before they are made. You can search databases of known fraudsters to detect repeat offenders and record all outcomes, referrals and suspects within the system.
Gain a consolidated view of fraud risk.
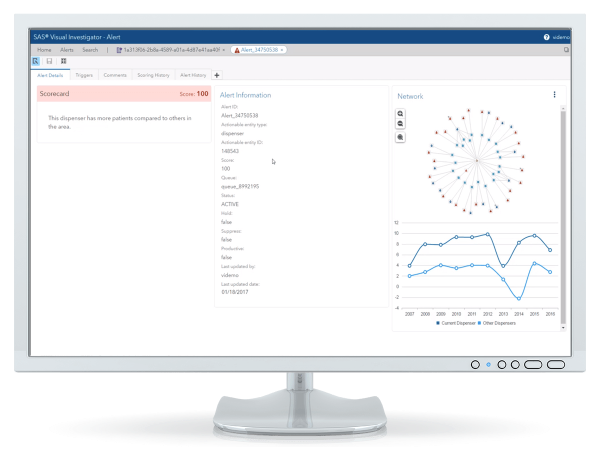
Identify linkages among seemingly unrelated individuals and activities with a unique visualization interface that lets you analyze all related activities and relationships at a network dimension. Get a better understanding of new threats and prevent big losses early using social network diagrams and sophisticated data mining capabilities. The solution's search and discovery capabilities let you perform free-text, field-based or geospatial searches across all internal and external data, as well as refine searches using interactive filters and facets designed for investigators. And you can continually improve models and adapt the system to address changing fraud trends.


Increase efficiency and reduce costs.
Risk- and value-based scoring models accurately score and prioritize alerts before they go to investigators. This increases the ROI of investigators by ensuring they are working on the highest-value cases. A configurable workflow and intelligent case management tools enable you to systematically investigate, capture and display all information pertinent to a case, including interview notes and evidence needed for criminal or civil prosecution, restitution and collections. Auditing information related to user activities is captured automatically by the system, and you can configure the level of detail captured to meet your compliance needs.
Key Features
A single, end-to-end framework uses multiple techniques – automated business rules, predictive modeling, text mining, exception reporting, network link analysis, etc. – to better identify fraudulent activity and stop payments before they are made.
Data management
Integrates data from any internal or external source – watch lists, third parties, unstructured text, etc. – regardless of system or format, and integrates seamlessly with existing rules engines.
Advanced analytics with embedded AI
Provides a broad set of advanced analytic and AI techniques, including modern statistical, machine learning, deep learning and text analytics algorithms.
Rule & analytic model management
Includes prepackaged heuristic rules, anomaly detection and predictive models and lets you create and logically manage business rules, analytic models, alerts and watch lists.
Detection & alert generation
Enables the systematic detection of suspicious activity using a fraud scoring engine that combines business rules, anomaly detection and advanced analytics to score transactions in real time.
Alert management
Combines alerts from multiple monitoring systems and associates them with common individuals for a more complete view of risk for individuals or groups.
Social network analysis
Provides a unique visualization interface that lets you go beyond transaction and account views to analyze related activities and relationships at a network dimension.
Search & discovery
Lets you perform free-text, field-based or geospatial searches across all data (internal and external), and refine searches using interactive filters.
Intelligent case management
Systematically facilitates investigative reviews using a configurable workflow and stores all information pertinent to a case.
Flexible deployment options
Choose your preferred deployment option – complete hosting by SAS, deployment at your site or a combination of the two. Offers highly secure hosting for your sensitive information. SAS is certified and experienced in handling sensitive medical (HIPAA), financial/personal (PII) and tax (IRS publication 1075) data.

